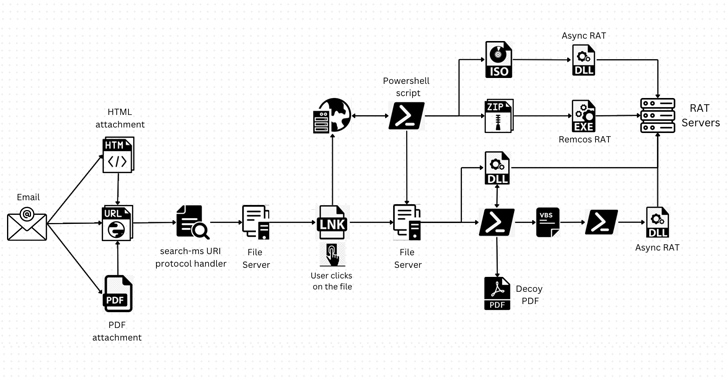
A legitimate Windows search feature is being exploited by malicious actors to download arbitrary payloads from remote servers and compromise targeted systems with remote access trojans such as AsyncRAT and Remcos RAT.
The novel attack technique, per Trellix, takes advantage of the “search-ms:” URI protocol handler, which offers the ability for applications and HTML links to launch custom local searches on a device, and the “search:” application protocol, a mechanism for calling the desktop search application on Windows.
“Attackers are directing users to websites that exploit the ‘search-ms’ functionality using JavaScript hosted on the page,” security researchers Mathanraj Thangaraju and Sijo Jacob said in a Thursday write-up. “This technique has even been extended to HTML attachments, expanding the attack surface.”
In such attacks, threat actors have been observed creating deceptive emails that embed hyperlinks or HTML attachments containing a URL that redirects users to compromised websites. This triggers the execution of JavaScript that makes use of the URI protocol handlers to perform searches on an attacker-controlled server.
It’s worth noting that clicking on the link also generates a warning “Open Windows Explorer?,” approving which “the search results of remotely hosted malicious shortcut files are displayed in Windows Explorer disguised as PDFs or other trusted icons, just like local search results,” the researchers explained.
“This smart technique conceals the fact that the user is being provided with remote files and gives the user the illusion of trust. As a result, the user is more likely to open the file, assuming it is from their own system, and unknowingly execute malicious code.”
Should a victim click on one of the shortcut files, it leads to the execution of a rogue dynamic-link library (DLL) using the regsvr32.exe utility.
In an alternative variant of the campaign, the shortcut files are employed to run PowerShell scripts, which, in turn, download additional payloads in the background, while displaying a decoy PDF document to deceive victims.
Regardless of the method used, the infections lead to the installation of AsyncRAT and Remcos RAT that can be used by the threat actors to remotely commandeer the hosts, steal sensitive information, and even sell the access to other attackers.
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
With Microsoft steadily taking steps to clamp down on various initial access vectors, it’s expected that adversaries could latch onto the URI protocol handler method to evade traditional security defenses and distribute malware.
“It is crucial to refrain from clicking on suspicious URLs or downloading files from unknown sources, as these actions can expose systems to malicious payloads delivered through the ‘search’ / ‘search-ms’ URI protocol handler,” the researchers said.





