Microsoft Word documents exploiting known remote code execution flaws are being used as phishing lures to drop malware called LokiBot on compromised systems.
“LokiBot, also known as Loki PWS, has been a well-known information-stealing Trojan active since 2015,” Fortinet FortiGuard Labs researcher Cara Lin said. “It primarily targets Windows systems and aims to gather sensitive information from infected machines.”
The cybersecurity company, which spotted the campaign in May 2023, said the attacks take advantage of CVE-2021-40444 and CVE-2022-30190 (aka Follina) to achieve code execution.
The Word file that weaponizes CVE-2021-40444 contains an external GoFile link embedded within an XML file that leads to the download of an HTML file, which exploits Follina to download a next-stage payload, an injector module written in Visual Basic that decrypts and launches LokiBot.
The injector also features evasion techniques to check for the presence of debuggers and determine if it’s running in a virtualized environment.
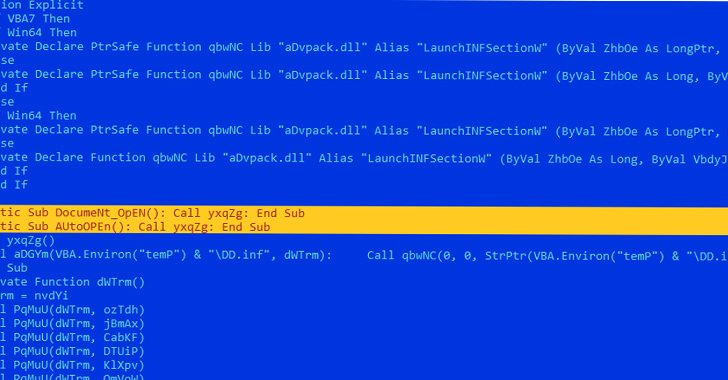
An alternative chain discovered towards the end of May starts with a Word document incorporating a VBA script that executes a macro immediately upon opening the document using the “Auto_Open” and “Document_Open” functions.
The macro script subsequently acts as a conduit to deliver an interim payload from a remote server, which also functions as an injector to load LokiBot and connect to a command-and-control (C2) server.
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
LokiBot, not to be confused with an Android banking trojan of the same name, comes with capabilities to log keystrokes, capture screenshots, gather login credential information from web browsers, and siphon data from a variety of cryptocurrency wallets.
“LokiBot is a long-standing and widespread malware active for many years,” Lin said. “Its functionalities have matured over time, making it easy for cybercriminals to use it to steal sensitive data from victims. The attackers behind LokiBot continually update their initial access methods, allowing their malware campaign to find more efficient ways to spread and infect systems.”






