As many as 196 hosts have been infected as part of an aggressive cloud campaign mounted by the TeamTNT group called Silentbob.
“The botnet run by TeamTNT has set its sights on Docker and Kubernetes environments, Redis servers, Postgres databases, Hadoop clusters, Tomcat and Nginx servers, Weave Scope, SSH, and Jupyter applications,” Aqua security researchers Ofek Itach and Assaf Morag said in a report shared with The Hacker News.
“The focus this time seems to be more on infecting systems and testing the botnet, rather than deploying cryptominers for profit.”
The development arrives a week after the cloud security company detailed an intrusion set linked to the TeamTNT group that targets exposed JupyterLab and Docker APIs to deploy the Tsunami malware and hijack system resources to run a cryptocurrency miner.
The latest findings suggest a broader campaign and the use of a larger attack infrastructure than previously thought, including various shell scripts to steal credentials, deploy SSH backdoors, download additional payloads, and drop legitimate tools like kubectl, Pacu, and Peirates to conduct reconnaissance of the cloud environment.
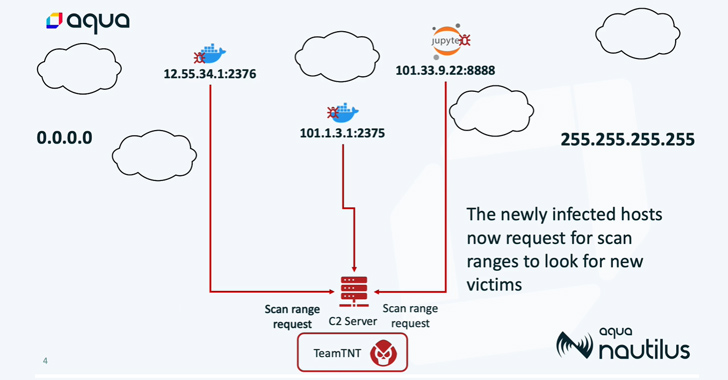
The attack chains are realized through the deployment of rogue container images hosted on Docker Hub, which are designed to scan the internet for misconfigured instances and infect the newly identified victims with Tsunami and a worm script to co-opt more machines into a botnet.
“This botnet is notably aggressive, rapidly proliferating across the cloud and targeting a wide array of services and applications within the Software Development Life Cycle (SDLC),” the researchers said. “It operates at an impressive speed, demonstrating remarkable scanning capability.”
Tsunami uses the Internet Relay Chat (IRC) protocol to connect to the command-and-control (C2) server, which then issues commands to all the infected hosts under its control, thereby allowing the threat actor to maintain backdoor access.
What’s more, the cryptomining execution is hidden using a rootkit called prochider to prevent it from being detected when a ps command is run on the hacked system to retrieve the list of active processes.
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
“TeamTNT is scanning for credentials across multiple cloud environments, including AWS, Azure, and GCP,” the researchers said. It’s the latest evidence that the threat actors are upgrading their tradecraft.
“They are not only looking for general credentials but also specific applications such as Grafana, Kubernetes, Docker Compose, Git access, and NPM. Additionally, they are searching for databases and storage systems such as Postgres, AWS S3, Filezilla, and SQLite.”
The development comes days after Sysdig disclosed a new attack mounted by SCARLETEEL to compromise AWS infrastructure with the goal of conducting data theft and distributing cryptocurrency miners on compromised systems.
While there were circumstantial links connecting SCARLETEEL to TeamTNT, Aqua told The Hacker News that the intrusion set is in fact linked to the threat actor.
“This is another campaign by TeamTNT,” Morag, lead data analyst at Aqua Nautilus research team, said. “The SCARLETEEL IP address, 45.9.148[.]221, was used just days ago in TeamTNT’s IRC channel C2 server. The scripts are very similar and the TTPs are the same. It looks like TeamTNT never stopped attacking. If they ever retired, it was only for a brief moment.”






