.jpg)
Charming Kitten, the nation-state actor affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC), has been attributed to a bespoke spear-phishing campaign that delivers an updated version of a fully-featured PowerShell backdoor called POWERSTAR.
“There have been improved operational security measures placed in the malware to make it more difficult to analyze and collect intelligence,” Volexity researchers Ankur Saini and Charlie Gardner said in a report published this week.
The threat actor is something of an expert when it comes to employing social engineering to lure targets, often crafting tailored fake personas on social media platforms and engaging in sustained conversations to build rapport before sending a malicious link. It’s also tracked under the names APT35, Cobalt Illusion, Mint Sandstorm (formerly Phosphorus), and Yellow Garuda.
Recent intrusions orchestrated by Charming Kitten have made use of other implants such as PowerLess and BellaCiao, suggesting that the group is utilizing an array of espionage tools at its disposal to realize its strategic objectives.
POWERSTAR is another addition to the group’s arsenal. Also called CharmPower, the backdoor was first publicly documented by Check Point in January 2022, uncovering its use in connection with attacks weaponizing the Log4Shell vulnerabilities in publicly-exposed Java applications.
It has since been put to use in at least two other campaigns, as documented by PwC in July 2022 and Microsoft in April 2023.
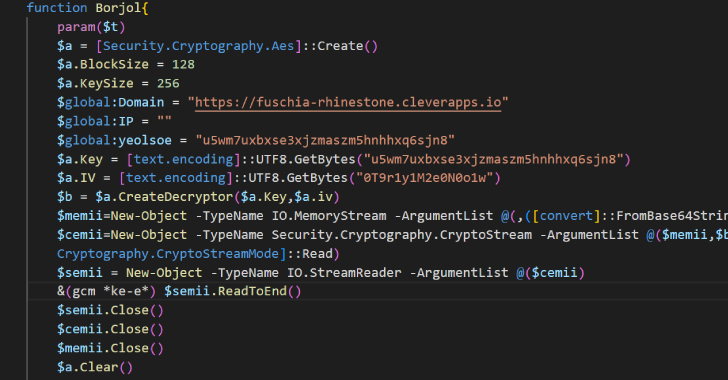
Volexity, which detected a rudimentary variant of POWERSTAR in 2021 distributed by a malicious macro embedded in DOCM file, said the May 2023 attack wave leverages an LNK file inside a password-protected RAR file to download the backdoor from Backblaze, while also taking steps to hinder analysis.
“With POWERSTAR, Charming Kitten sought to limit the risk of exposing their malware to analysis and detection by delivering the decryption method separately from the initial code and never writing it to disk,” the researchers said.
“This has the added bonus of acting as an operational guardrail, as decoupling the decryption method from its command-and-control (C2) server prevents future successful decryption of the corresponding POWERSTAR payload.”
The backdoor comes with an extensive set of features that enable it to remotely execute PowerShell and C# commands, set up persistence, collect system information, and download and execute more modules to enumerate running processes, capture screenshots, search for files matching specific extensions, and monitor if persistence components are still intact.
Also improved and expanded from the earlier version is the cleanup module that’s designed to erase all traces of the malware’s footprint as well as delete persistence-related registry keys. These updates point to Charming Kitten’s continued efforts to refine its techniques and evade detection.
Volexity said it also detected a different variant of POWERSTAR that attempts to retrieve a hard-coded C2 server by decoding a file stored on the decentralized InterPlanetary Filesystem (IPFS), signaling an attempt to make its attack infrastructure more resilient.
The development coincides with a MuddyWater’s (aka Static Kitten) use of previously undocumented command-and-control (C2) framework called PhonyC2 to deliver malicious payload to compromised hosts.
“The general phishing playbook used by Charming Kitten and the overall purpose of POWERSTAR remain consistent,” the researchers said. “The references to persistence mechanisms and executable payloads within the POWERSTAR Cleanup module strongly suggests a broader set of tools used by Charming Kitten to conduct malware-enabled espionage.”






