The Iranian state-sponsored group dubbed MuddyWater has been attributed to a previously unseen command-and-control (C2) framework called PhonyC2 that’s been put to use by the actor since 2021.
Evidence shows that the custom made, actively developed framework has been leveraged in the February 2023 attack on Technion, an Israeli research institute, cybersecurity firm Deep Instinct said in a report shared with The Hacker News.
What’s more, additional links have been unearthed between the Python 3-based program and other attacks carried out by MuddyWater, including the ongoing exploitation of PaperCut servers.
“It is structurally and functionally similar to MuddyC3, a previous MuddyWater custom C2 framework that was written in Python 2,” security researcher Simon Kenin said. “MuddyWater is continuously updating the PhonyC2 framework and changing TTPs to avoid detection.”
MuddyWater, also known as Mango Sandstorm (previously Mercury), is a cyber espionage group that’s known to operate on behalf of Iran’s Ministry of Intelligence and Security (MOIS) since at least 2017.
The findings arrive nearly three months after Microsoft implicated the threat actor for carrying out destructive attacks on hybrid environments, while also calling out its collaboration with a related cluster tracked as Storm-1084 (aka DEV-1084 or DarkBit) for reconnaissance, persistence, and lateral movement.
“Iran conducts cyber operations aiming at intelligence collection for strategic purposes, essentially targeting neighboring states, in particular Iran’s geopolitical rivals such as Israel, Saudi Arabia, and Arabic Gulf countries, a continued focus observed in all operations since 2011,” French cybersecurity company Sekoia said in an overview of pro-Iranian government cyber attacks.
Attack chains orchestrated by the group, like other Iran-nexus intrusion sets, employ vulnerable public-facing servers and social engineering as the primary initial access points to breach targets of interest.
“These include the use of charismatic sock puppets, the lure of prospective job opportunities, solicitation by journalists, and masquerading as think tank experts seeking opinions,” Recorded Future noted last year. “The use of social engineering is a central component of Iranian APT tradecraft when engaging in cyber espionage and information operations.”
Deep Instinct said it discovered the PhonyC2 framework in April 2023 on a server that’s related to broader infrastructure put to use by MuddyWater in its attack targeting Technion earlier this year. The same server was also found to host Ligolo, a staple reverse tunneling tool utilized by the threat actor.
The connection stems from the artifact names “C:programdatadb.sqlite” and “C:programdatadb.ps1,” which Microsoft described as customized PowerShell backdoors used by MuddyWater and which are dynamically generated via the PhonyC2 framework for execution on the infected host.
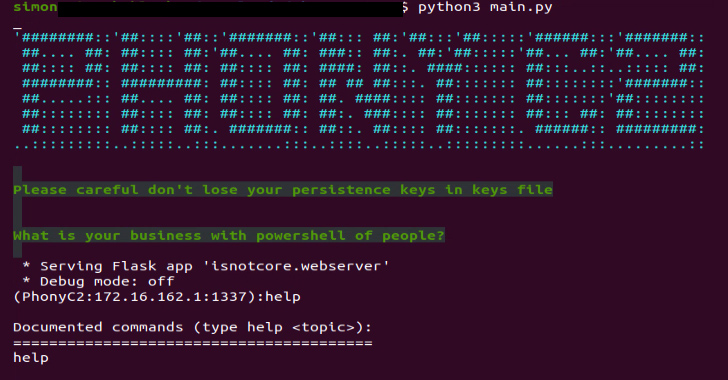
PhonyC2 is a “post-exploitation framework used to generate various payloads that connect back to the C2 and wait for instructions from the operator to conduct the final step of the ‘intrusion kill chain,'” Kenin said, calling it a successor to MuddyC3 and POWERSTATS.
Some of the the notable commands supported by the framework are as follows –
- payload: Generate the payloads “C:programdatadb.sqlite” and “C:programdatadb.ps1” as well as a PowerShell command to execute db.ps1, which, in turn, executes db.sqlite
- droper: Create different variants of PowerShell commands to generate “C:programdatadb.sqlite” by reaching out to the C2 server and writing the encoded contents sent by the server to the file
- Ex3cut3: Create different variants of PowerShell commands to generate “C:programdatadb.ps1” — a script that contains the logic to decode db.sqlite — and the final-stage
- list: Enumerate all connected machines to the C2 server
- setcommandforall: Execute the same command across all connected hosts simultaneously
- use: Get a PowerShell shell on a remote computer to run more commands
- persist: Generate a PowerShell code to enable the operator to gain persistence on the infected host so it will connect back to the server upon a restart
“The framework generates for the operator different powershell payloads,” Mark Vaitzman, threat research team leader at Deep Instinct told The Hacker News. “The operator needs to have initial access to a victim machine to execute them. Some of the generated payloads connect back to the operator C2 to allow persistence.”
Muddywater is far from the only Iranian nation-state group to train its eyes on Israel. In recent months, various entities in the country have been targeted by at least three different actors such as Charming Kitten (aka APT35), Imperial Kitten (aka Tortoiseshell), and Agrius (aka Pink Sandstorm).
“The C2 is what connects the initial phase of the attack to the final step,” Vaitzman said. “For MuddyWater, the C2 framework is very important as it allows them to stay stealthy and collect data from the victims. This is not the first or last custom C2 framework they use during major attacks.”








