Cybersecurity researchers have exposed the workings of a scam ring called CryptosLabs that’s estimated to have made €480 million in illegal profits by targeting users in French-speaking individuals in France, Belgium, and Luxembourg since April 2018.
The syndicate’s massive fake investment schemes primarily involve impersonating 40 well-known banks, fin-techs, asset management firms, and crypto platforms, setting up a scam infrastructure spanning over 350 domains hosted on more than 80 servers, Group-IB said in a deep-dive report.
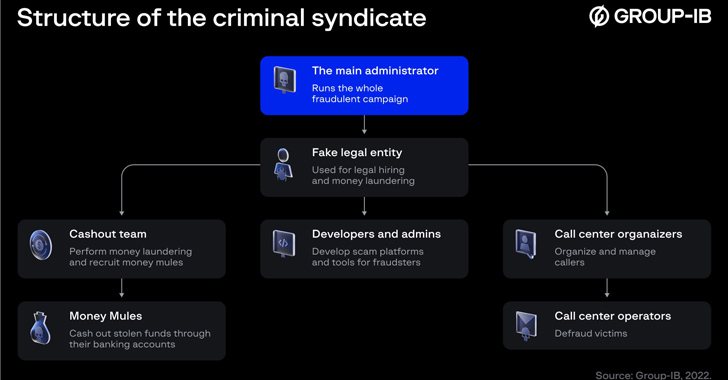
The Singapore-headquartered company described the criminal outfit as “operated by a hierarchy of kingpins, sales agents, developers, and call center operators” who are recruited to ensnare potential victims by promising high returns on their capital.
“CryptoLabs made their scam schemes more convincing through region-focused tactics, such as hiring French-speaking callers as ‘managers’ and creating fake landing pages, social media ads, documents, and investment platforms in the French language,” Anton Ushakov, deputy head of Group-IB’s high-tech crime investigation department in Amsterdam, said.
“They even impersonated French-dominant businesses to resonate with their target audience better and be successful in exploiting them.”
It all starts with luring targets through advertisements on social media, search engines, and forums dedicated to online investments, masquerading as an “investment division” of the impersonated organization and presenting them with attractive investment plans in an attempt to part with their contact details.
In the next stage, they are approached by call center operators who provide additional details about the bogus platform and the credentials required to conduct trading.
“After logging in, the victims deposit funds on a virtual balance,” Ushakov said. “They are then shown fictitious performance charts that trigger them to invest more for better profits until they realize they cannot withdraw any funds even when paying the ‘release fees.'”
While the initial deposits are to the tune of €200-300, the scam is engineered to incentivize victims into depositing more funds by showcasing an illusion of good investment results.
Group-IB, which first shed light on the large-scale scam-as-a-service operation in December 2022, said it was able to trace the first signs of the group’s activity dating back to 2015, when it was found experimenting with different landing pages. CryptosLabs’ tryst with investment scams would begin in earnest around June 2018 after a two-month preparation.
A crucial selling point of the campaign is the use of a custom scam kit that allows the threat actors to run, manage, and scale their activities at different stages, right from rogue advertisements on social media to the website templates used to pull off the heist.
Also part of the kit are auxiliary tools to build landing pages, a customer relationship management (CRM) service that enables the addition of new managers to each domain, a leads control panel that could be used by scammers to onboard new customers to the trading platform, and a VoIP utility to communicate with victims in real-time.
“Analyzing CryptosLabs, it is evident that the threat group has given its activities a well-established structure in terms of operations and headcount, and is likely to expand the scope and scale of its illicit business in the coming years,” Ushakov said.





