A ransomware threat called 8Base that has been operating under the radar for over a year has been attributed to a “massive spike in activity” in May and June 2023.
“The group utilizes encryption paired with ‘name-and-shame’ techniques to compel their victims to pay their ransoms,” VMware Carbon Black researchers Deborah Snyder and Fae Carlisle said in a report shared with The Hacker News. “8Base has an opportunistic pattern of compromise with recent victims spanning across varied industries.”
8Base, according to statistics gathered by Malwarebytes and NCC Group, has been linked to 67 attacks as of May 2023, with about 50% of the victims operating in the business services, manufacturing, and construction sectors. A majority of the targeted companies are located in the U.S. and Brazil.
With very little known about the operators of the ransomware, its origins remain something of a cipher. What’s evident is that it has been active since at least March 2022 and the actors describe themselves as “simple pentesters.”
VMware said 8Base is “strikingly” similar to that of another data extortion group tracked as RansomHouse, citing overlaps in the ransom notes dropped on compromised machines and the language used in the respective data leak portals.
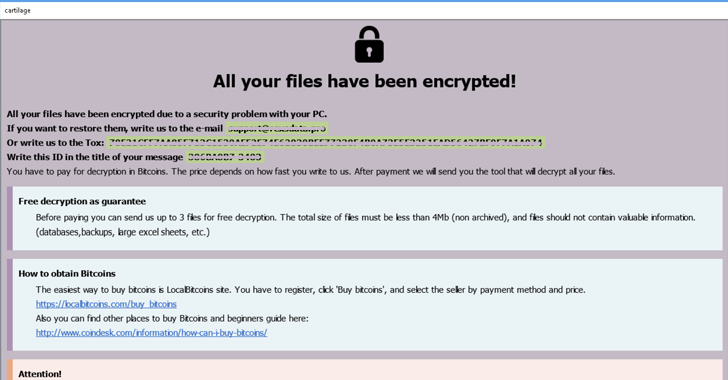
“The verbiage is copied word for word from RansomHouse’s welcome page to 8Base’s welcome page,” the researchers said. “This is the case for their Terms of Service pages and FAQ pages.”
A comparison of the two threat groups reveals that while RansomHouse openly advertises their partnerships, 8Base does not. Another crucial differentiator is their leak pages.
But in an interesting twist, VMware noted that it was able to identify a Phobos ransomware that uses the “.8base” file extension for encrypted files, raising the possibility that 8Base could be a successor to Phobos or that the attackers are simply making use of already existing ransomware strains without having to develop their own custom locker.
“The speed and efficiency of 8Base’s current operations does not indicate the start of a new group but rather signifies the continuation of a well-established mature organization,” the researchers said. “Whether 8Base is an offshoot of Phobos or RansomHouse remains to be seen.”
8Base is part of a wave of ransomware newbies entering the market such as CryptNet, Xollam, and Mallox, even as known families like BlackCat, LockBit, and Trigona have witnessed continuous updates to their features and attack chains to broaden their horizons beyond Windows to infect Linux and macOS systems.
One instance highlighted by Cyble entails the use of BATLOADER to deploy Mallox, suggesting that the threat actors are actively refining their tactics to “enhance evasiveness and maintain their malicious activities.”
“Groups adopt other groups’ code, and affiliates — which can be considered cybercrime groups in their own right — switch between different types of malware,” Kaspersky said in an analysis last week. “Groups work on upgrades to their malware, adding features and providing support for multiple, previously unsupported, platforms, a trend that existed for some time now.”





