South Korean education, construction, diplomatic, and political institutions are at the receiving end of new attacks perpetrated by a China-aligned threat actor known as the Tonto Team.
“Recent cases have revealed that the group is using a file related to anti-malware products to ultimately execute their malicious attacks,” the AhnLab Security Emergency Response Center (ASEC) said in a report published this week.
Tonto Team, active since at least 2009, has a track record of targeting various sectors across Asia and Eastern Europe. Earlier this year, the group was attributed to an unsuccessful phishing attack on cybersecurity company Group-IB.
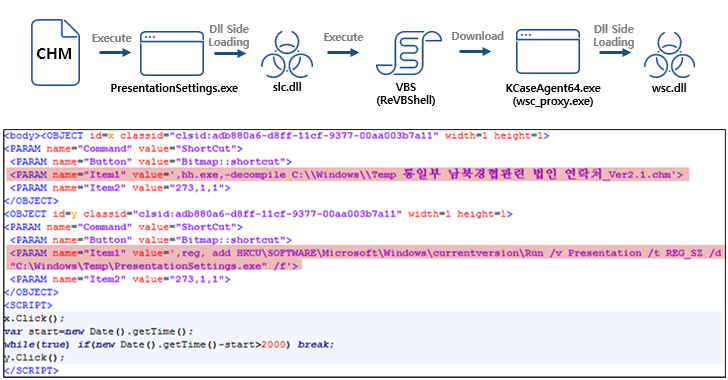
The attack sequence discovered by ASEC starts with a Microsoft Compiled HTML Help (.CHM) file that executes a binary file to side-load a malicious DLL file (slc.dll) and launch ReVBShell, an open source VBScript backdoor also put to use by another Chinese threat actor called Tick.
ReVBShell is subsequently leveraged to download a second executable, a legitimate Avast software configuration file (wsc_proxy.exe), to side-load a second rogue DLL (wsc.dll), ultimately leading to the deployment of the Bisonal remote access trojan.
“The Tonto Team is constantly evolving through various means such as using normal software for more elaborate attacks,” ASEC said.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
The use of CHM files as a distribution vector for malware is not limited to Chinese threat actors alone. Similar attack chains have been adopted by a North Korean nation-state group known as ScarCruft in attacks aimed at its southern counterpart to backdoor targeted hosts.
The adversary, also known as APT37, Reaper, and Ricochet Chollima, has since also utilized LNK files to distribute the RokRAT malware, which is capable of collecting user credentials and downloading additional payloads.





