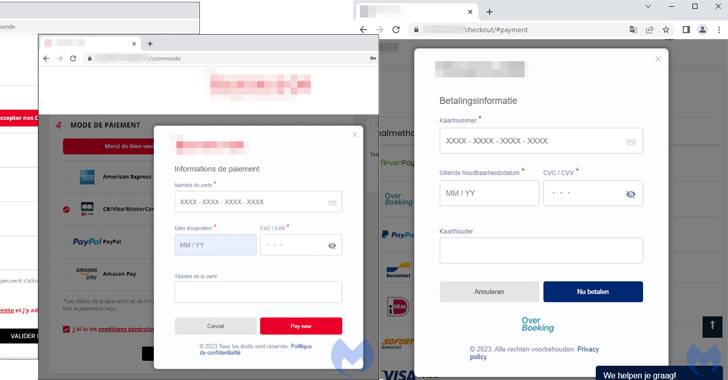
An ongoing Magecart campaign has attracted the attention of cybersecurity researchers for leveraging realistic-looking fake payment screens to capture sensitive data entered by unsuspecting users.
“The threat actor used original logos from the compromised store and customized a web element known as a modal to perfectly hijack the checkout page,” Jérôme Segura, director of threat intelligence at Malwarebytes, said. “The remarkable thing here is that the skimmer looks more authentic than the original payment page.”
The term Magecart is a catch-all that refers to several cybercrime groups which employ online skimming techniques to steal personal data from websites – most commonly, customer details and payment information on e-commerce websites.
The name originates from the groups’ initial targeting of the Magento platform. According to data shared by Sansec, the first Magecart-like attacks were observed as early as 2010. As of 2022, more than 70,000 stores are estimated to have been compromised with a web skimmer.
These digital skimming attacks, also called formjacking, traditionally leverage various kinds of JavaScript trickery to siphon sensitive information from website users.
The latest iteration, as observed by Malwarebytes on an unnamed Parisian travel accessory store running on the PrestaShop CMS, involved the injection of a skimmer called Kritec to intercept the checkout process and display a fake payment dialog to victims.
Kritec, previously detailed by Akamai and Malwarebytes in February 2023, has been found to impersonate legitimate third-party vendors like Google Tag Manager as an evasion technique.
The cybersecurity firm said the skimmer is both complex and heavily obfuscated, with the malicious modal loaded upon selecting a credit card as the payment option from the compromised website.
Once the payment card details are harvested, a fake error message about payment cancellation is briefly displayed to the victim before redirecting to the actual payment page, at which point the payment will go through.
“The skimmer will drop a cookie which will serve as an indication that the current session is now marked as completed,” Segura explained. “If the user was to go back and attempt the payment again, the malicious modal would no longer be displayed.”
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
The threat actors behind the operation are said to be using different domains to host the skimmer, which are given similar names: “[name of store]-loader.js,” suggesting that the attacks are targeting different online stores with custom modals.
“Discerning whether an online store is trustworthy has become very difficult and this case is a good example of a skimmer that would not raise any suspicion,” Segura said.
The findings come a little over two months after Malwarebytes unearthed another web skimmer that collects browser fingerprint data, such as IP addresses and User-Agent strings, along with credit card information, likely in an attempt to monitor invalid users such as bots and security researchers.







