The threat actor behind the information-stealing malware known as Typhon Reborn has resurfaced with an updated version (V2) that packs in improved capabilities to evade detection and resist analysis.
The new version is offered for sale on the criminal underground for $59 per month, $360 per year, or alternatively, for $540 for a lifetime subscription.
“The stealer can harvest and exfiltrate sensitive information and uses the Telegram API to send stolen data to attackers,” Cisco Talos researcher Edmund Brumaghin said in a Tuesday report.
Typhon was first documented by Cyble in August 2022, detailing its myriad features, including hijacking clipboard content, capturing screenshots, logging keystrokes, and stealing data from crypto wallet, messaging, FTP, VPN, browser, and gaming apps.
Based on another stealer malware called Prynt Stealer, Typhon is also capable of delivering the XMRig cryptocurrency miner. In November 2022, Palo Alto Networks Unit 42 unearthed an updated version dubbed Typhon Reborn.
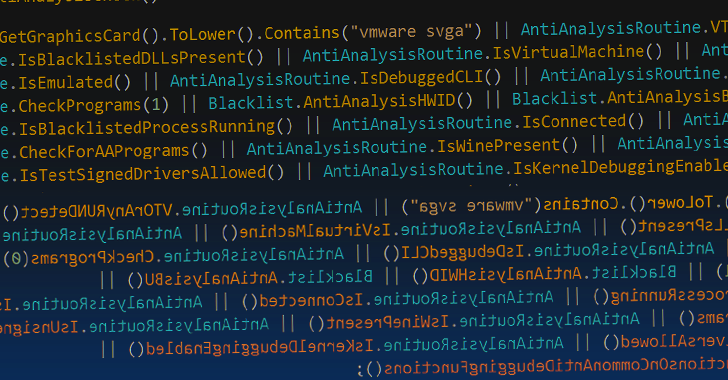
“This new version has increased anti-analysis techniques and it was modified to improve the stealer and file grabber features,” Unit 42 said, pointing out the removal of existing features like keylogging and cryptocurrency mining in an apparent attempt to lower the chances of detection.
The latest V2 variant, per Cisco Talos, was marketed by its developer on January 31, 2023, on the Russian language dark web forum XSS.
“Typhon Reborn stealer is a heavily refactored and improved version of the older and unstable Typhon Stealer,” the malware author said, in addition to touting its inexpensive price and the absence of any backdoors.
Like other malware, V2 comes with options to avoid infecting systems that are located in the Commonwealth of Independent States (CIS) countries. It, however, notably excludes Ukraine and Georgia from the list.
Besides incorporating more anti-analysis and anti-virtualization checks, Typhon Reborn V2 removes its persistence features, instead opting to terminate itself after exfiltrating the data.
The malware ultimately transmits the collected data in a compressed archive via HTTPS using the Telegram API, marking continued abuse of the messaging platform.
“Once the data has been successfully transmitted to the attacker, the archive is then deleted from the infected system,” Brumaghin said. “The malware then calls [a self-delete function] to terminate execution.”
Learn to Secure the Identity Perimeter – Proven Strategies
Improve your business security with our upcoming expert-led cybersecurity webinar: Explore Identity Perimeter strategies!
The findings come as Cyble disclosed a new Python-based stealer malware named Creal that targets cryptocurrency users via phishing sites mimicking legitimate crypto mining services like Kryptex.
The malware is no different from Typhon Reborn in that it’s equipped to siphon cookies and passwords from Chromium-based web browsers as well as data from instant messaging, gaming, and crypto wallet apps.
That said, the malware’s source code is available on GitHub, thereby allowing other threat actors to alter the malware to suit their needs and making it a potent threat.
“Creal Stealer is capable of exfiltrating data using Discord webhooks and multiple file-hosting and sharing platforms such as Anonfiles and Gofile,” Cyble said in a report published last week.
“The trend of using open source code in malware is increasing among cybercriminals, since it allows them to create sophisticated and customized attacks with minimal expenses.”





